The Irrevocable SSL certificates of CloudFlare
Posted in: Technology
I moved this website “worldofmatthew.com” away from CloudFlare back in August 2020.
That should have been the end of the relation with CloudFlare for my website.
Unfortunately, while I was moving the L7 Anti-DDOS protection to path.net (via a reseller), I checked the SSL Transparency and noticed that CloudFlare still had a vaild SSL certificate for this website.
Even worse, this CloudFlare certificate lasts for a year, meaning they have a SSL certificate for this website, until June 2021.
Irrevocable SSL Certificates by CloudFlare
This website currently uses path.net for DDOS migration. Just like CloudFlare, they have their own SSL certificate for this website. As they require it to MITM website requests to block anyone trying to perform an L7 attack.
The difference is that path.net uses Let’s Encrypt, which would allow me to revoke their SSL certificate for this website. All I would have to do is to download the public key and present that with an Acme challenge and then I can revoke it.
You would think that it would be possible to get a CloudFlare SSL certificate revoked?
How about No?
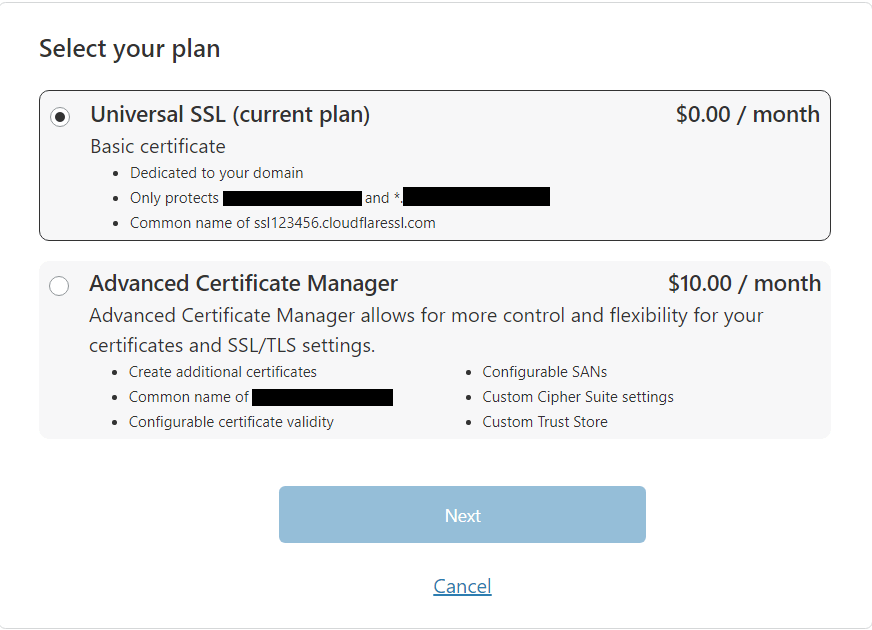
Well. Unless you want to pay CloudFlare $10 per month to gain access to the “Advanced Certificate Manager”.
This would give access to use a custom Let’s Encrypt. This would also allow you to set your SSL certificate validity period to as low as 14 days, rather than a year on the free “Universal SSL”.
Basically, it is a case of pay CloudFlare $10 per month or they get 100% control over your SSL certificate and will deny your requests to revoke.
In fact, the official stance of the SSL team at CloudFlare is that they won’t revoke unless the team has “determined the private key was compromised.”
Isn’t this sounding pretty corrupt?
Yes….
You blindly trust that CloudFlare will delete the SSL certificate upon leaving. They will provide you zero evidence of them of actually deleting the certificate.
This is from a CDN who has a level of access unmatched by their rivals. CloudFlare are becoming the defualt DNS for browsers and have a VPN service.
You have to trust them to never abuse that power.
Even worse, as they forcibly keep a working SSL certificate, they don’t even have to generate a new one. Meaning, SSL transparency WILL NOT show anything if CloudFlare ever decide to hijack and MITM traffic to your website.
If someone asks that a SSL certificate is revoked after leaving it, revoke it. The webmaster is no longer giving them permission to have a SSL certificate for their domain.
By not allowing for SSL certificates to be revoked, CloudFlare is in effect holding them hostage. It must not be the job of a Certificate authority to refuse such requests.
Most Certificate authorities would never lock a webmaster out of control of a SSL certificate for their domain.
They also would not tell people to pay of $10/month for get rights to revoke a Certificate.
This comes to a question of whether CloudFlare should even be in SSL chain-of-trust.
I requested for them to revoke, by not revoking Cloudflare are keeping an active SSL Certificate without my permission. I think such behavior should make browsers question if they can keep Cloudflare in their chain-of-trust.
Published: 20th January 2021

 Home Page
Home Page The Blog
The Blog Technology
Technology Matthew's Reviews
Matthew's Reviews Matthew's Gaming World
Matthew's Gaming World Tor (Onion Site)
Tor (Onion Site)